Setting up a Samba 4 Domain Controller on Debian 9
Posted on Mon 11 February 2019 in blog
Let's set up Samba 4 to serve as an Active Directory (AD) Domain Controller (DC) on Debian 9.
Prerequisites
We'll start with a headless install of Debian 9, selecting only "SSH server" and "standard system utilities" during Software selection.
We'll also assume that your server is set up with the following:
- Static IP address (although a DHCP reservation also works)
- Working DNS
- Working NTP
In this walkthrough, I'll be using the following configuration:
- NetBIOS domain (workgroup):
ONTHEFIVE - AD DNS domain:
ad.onthefive.com- Kerberos realm is therefore
AD.ONTHEFIVE.COM - DNS for the AD domain will be delegated to the DC (main DNS provided by another server)
- Additional UPN Suffix:
onthefive.com
- Kerberos realm is therefore
- DC hostname:
samba-dc
Note that I've followed industry best practices by selecting a sub-domain of my
primary domain (ad.onthefive.com) to serve as the AD domain. I will also add
onthefive.com as an additional User Principal Name (UPN) Suffix so usernames
will match email addresses (and generally just look better).
Procedure
Package Installation
Simply installing the samba package includes almost everything we will need.
It does not, however, include winbind which is essential1. We'll also want
smbclient and krb5-user for local testing of AD services.
apt install samba smbclient krb5-user winbind
When krb5-user is being set up, it will prompt you for the default Kerberos
realm. You can ignore this, as we will blow the configuration away later.
Samba uses the MIT KDC provided by your operating system if you run Samba 4.7 or later and has been built using the
--with-system-mitkrb5option. In other cases Samba uses the Heimdal KDC included in Samba.
Debian 9 ships with Version 4.5.12-Debian, so we'll be using the built-in
Heimdal KDC.
Intermediate steps
First, we need to remove the existing smb.conf:
(cd /etc/samba && mv smb.conf smb.conf.orig)
Next, we need to adjust the Debian default settings for the samba services.
By default, systemd is set up to run smbd, nmbd, and windbind as separate
services, but we want to run the Samba AD DC service.
systemctl stop smbd nmbd winbind
systemctl disable smbd nmbd winbind
systemctl mask smbd nmbd winbind
systemctl unmask samba-ad-dc
systemctl enable samba-ad-dc
Provision
Now that everything is ready, let's provision our Domain Controller.
#!/bin/bash
################################################################################
# Config Options
# Kerberos realm -- also used (in lowercase) as AD DNS domain
REALM="AD.ONTHEFIVE.COM"
# NetBIOS domain name (Workgroup)
DOMAIN="onthefive"
# Initial Administrator password -- must meet complexity requirements
ADMINPASS="YourAdminPasswordGoesHere!1234"
################################################################################
set -e
smbconf="/etc/samba/smb.conf"
if [ -f $smbconf ]; then
echo "$smbconf exists; remove and try again."
exit 1
fi
samba-tool domain provision \
--use-rfc2307 \
--server-role=dc \
--dns-backend=SAMBA_INTERNAL \
--realm="${REALM}" \
--domain="${DOMAIN}" \
--adminpass="${ADMINPASS}"
Running that script, you should see output like this:
...
A Kerberos configuration suitable for Samba 4 has been generated at /var/lib/samba/private/krb5.conf
Setting up fake yp server settings
Once the above files are installed, your Samba4 server will be ready to use
Server Role: active directory domain controller
Hostname: samba-dc
NetBIOS Domain: ONTHEFIVE
DNS Domain: ad.onthefive.com
DOMAIN SID: S-1-5-21-1234567890-987654321-123456789
Now we'll copy the krb5.conf
kerberos config file:
mv /etc/krb5.conf /etc/krb5.conf.old
cp /var/lib/samba/private/krb5.conf /etc/krb5.conf
And finally, we'll start the Samba AD DC service:
systemctl start samba-ad-dc
Delegating DNS
If you haven't done so yet, you'll now need to delegate your AD DNS zone.
In other words, configure your site's DNS server to refer requests for the
ad.example.com sub-domain to this domain controller.
In pfSense, these are called "Domain Overrides".
Testing
Now we need to test several services of AD. These tests are taken from the Samba wiki.
DNS
We'll look up a few records in DNS to verify that the DNS server and delegation
are working. If any of these requests fail, we can append localhost to tell
host to try the local Samba DNS server, to narrow down the problem.
Look up the DC's AD DNS record:
# host -t A samba-dc.ad.onthefive.com
Now test the various SRV records used by AD:
# host -t SRV _ldap._tcp.ad.onthefive.com
# host -t SRV _kerberos._tcp.ad.onthefive.com
# host -t SRV _kerberos._udp.ad.onthefive.com
Kerberos
Request a Kerberos ticket for the domain admin account:
# kinit administrator
Password for administrator@AD.ONTHEFIVE.COM:
Warning: Your password will expire in 41 days on Sun 24 Mar 2019 11:38:22 PM EDT
List the cached Kerberos tickets:
# klist
Ticket cache: FILE:/tmp/krb5cc_0
Default principal: administrator@AD.ONTHEFIVE.COM
Valid starting Expires Service principal
02/10/2019 23:11:32 02/11/2019 09:11:32 krbtgt/AD.ONTHEFIVE.COM@AD.ONTHEFIVE.COM
renew until 02/11/2019 23:11:28
File Server
List all shares provided by the DC:
# smbclient -L localhost -U%
Domain=[ONTHEFIVE] OS=[Windows 6.1] Server=[Samba 4.5.12-Debian]
Sharename Type Comment
--------- ---- -------
netlogon Disk
sysvol Disk
IPC$ IPC IPC Service (Samba 4.5.12-Debian)
Domain=[ONTHEFIVE] OS=[Windows 6.1] Server=[Samba 4.5.12-Debian]
Server Comment
--------- -------
Workgroup Master
--------- -------
To verify authentication, connect to the netlogon share using the domain
administrator account:
# smbclient //localhost/netlogon -UAdministrator -c 'ls'
Enter Administrator's password:
Domain=[ONTHEFIVE] OS=[Windows 6.1] Server=[Samba 4.5.12-Debian]
. D 0 Sun Feb 10 22:38:11 2019
.. D 0 Sun Feb 10 22:38:22 2019
60631916 blocks of size 1024. 56430608 blocks available
In the Domain
Join
Now we're ready to join our first workstation to the domain! This process is easy and readily-accessible elsewhere, so I won't repeat it here.
You'll also want a Windows workstation with the Active Directory tools installed: Windows 7 – How to install the Active Directory Users and Computers tools
Domain Configuration
Now that we have a working domain, we need to take care of that UPN Suffix before we go about adding users. This, too, is well-documented elsewhere, but it's easy enough:
- Open Active Directory Domains and Trusts.
- Right-click Active Directory Domains and Trusts in the left pane and select Properties.
- On the UPN Suffixes tab, enter your UPN suffix and click Add:
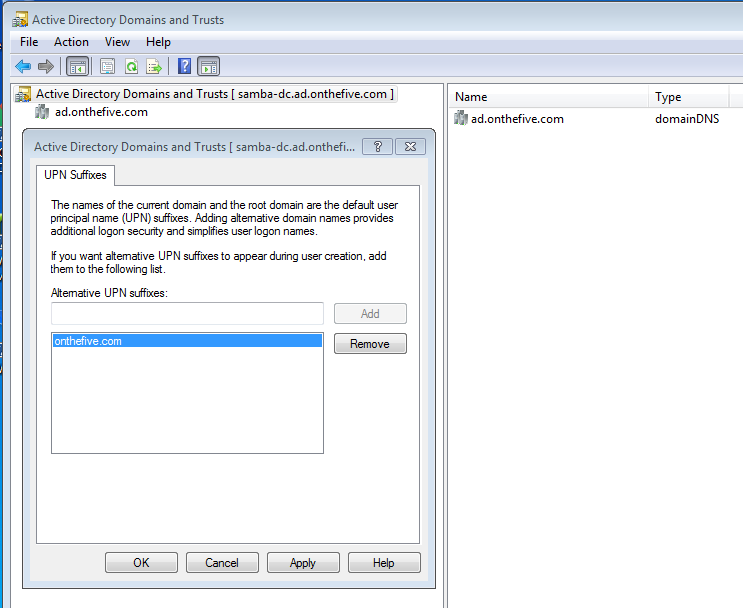
Now when you add a new user in Active Directory Users and Computers, you'll
be able to select the new UPN suffix:
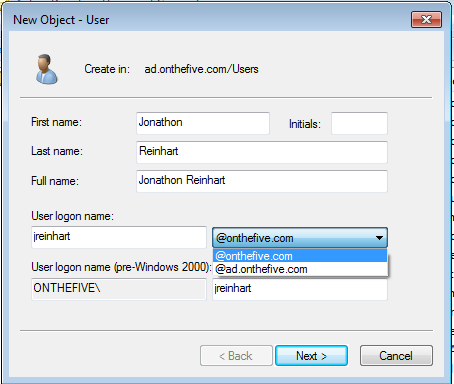
Unfortunately, there is no way to change the default UPN Suffix used by this tool.
That's it for now!
Footnotes
1 - winbind
I initially omitted winbind which was a big mistake. When trying to verify
the AD file server, I kept getting the error: session setup failed: NT_STATUS_INTERNAL_ERROR.
On the server I saw the following messages in /var/log/samba/log.smbd:
[2019/02/11 21:10:02.679757, 1] ../source3/smbd/sesssetup.c:290(reply_sesssetup_and_X_spnego)
Failed to generate session_info (user and group token) for session setup: NT_STATUS_INTERNAL_ERROR
I finally found this message on the Samba mailing list which clued me in to the problem.
