Configuring Winbind on a Samba AD DC on Debian 9
Posted on Tue 26 February 2019 in blog
In the previous post, we set up a Samba 4 DC. In this post, we'll configure Winbind on that Linux machine so all of the Samba-controlled UIDs/GIDs will resolve to their AD names. We'll also set things up so we can SSH and sudo appropriately.
Prerequisites
We'll assume that you already have a working Samba 4 DC on Debian 9.
Procedure
Package Installation
We'll install the following packages:
apt install libnss-winbind libpam-winbind
Winbindd Configuration
First, we'll configure the way that winbindd presents the home directory and
shell for users, by adding the following to the [global] section of
smb.conf:
template shell = /bin/bash
template homedir = /home/%D/%U
If you want, you could also use /home/%U to omit the domain part of home
directories.
Restart samba (systemctl restart samba-ad-dc.service).
Name Service Switch Configuration
Without updating NSS, you'll see UID/GID numbers that don't map to any known names:
# ls -l /var/lib/samba/sysvol
total 8
drwxrwx---+ 4 root 3000000 4096 Feb 10 22:38 ad.onthefive.com
Now we'll configure NSS to consult winbind about users and groups, by
appending winbind to the following database lines in /etc/nsswitch.conf:
passwd: compat winbind
group: compat winbind
NSS should become immediately aware of this change, and all consumers of the
getpwnam/getgrnam APIs from libc should be able to query names from
winbind.
The getent command-line
tool looks up entries in databases like passwd or group. We can call it
with AD names and expect results that look like this:
# getent passwd Administrator
ONTHEFIVE\administrator:*:0:100::/home/ONTHEFIVE/administrator:/bin/bash
# getent group 'Domain Admins'
ONTHEFIVE\domain admins:x:3000008:
Typical linux command-line tools are also now enlightened:
# ls -l /var/lib/samba/sysvol
total 8
drwxrwx---+ 4 root BUILTIN\administrators 4096 Feb 10 22:38 ad.onthefive.com
PAM Configuration
On my system, I didn't have to do anything to enable Winbind login via PAM. To
confirm that it's enabled, run pam-auth-update and ensure "Winbind NT/Active
Directory authentication" is selected.
You should now be able to SSH to your DC using any domain user:
ssh administrator@samba-dc
Note that Administrator actually maps to UID 0, which is also known as root:
$ ssh administrator@samba-dc
administrator@samba-dc's password:
root@samba-dc:~# id
uid=0(root) gid=100(users) groups=100(users),3000000(BUILTIN\administrators),3000004(ONTHEFIVE\group policy creator owners),3000005(ONTHEFIVE\denied rodc password replication group),3000006(ONTHEFIVE\enterprise admins),3000007(ONTHEFIVE\schema admins),3000008(ONTHEFIVE\domain admins),3000009(BUILTIN\users)
Automatic Home Directory Creation
If you log in as an AD user, you'll see an error from Bash that it Could not
chdir to home directory .... To improve this, we can ask PAM to create local
home directories upon user login, via
pam_mkhomedir.
On Debian, the libpam-runtime
package provides a script called pam-auth-update which uses templates from
/usr/share/pam-configs to make enabling PAM modules very easy. The
pam_mkhomedir.so module is provided by
libpam-modules.
Unfortunately, (as of 1.1.8-3.6) there is no pam-config for mkhomedir.
(See Debian bug 568577.)
However, we can simply download the file ourselves:
wget -O /usr/share/pam-configs/mkhomedir https://browse.dgit.debian.org/pam.git/plain/debian/pam-configs/mkhomedir?h=debian/1.1.8-4
Now you can run pam-auth-update and select "Create home directory on login".
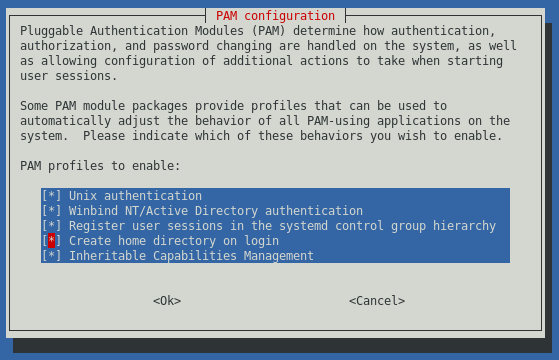
After logging in you should now have a valid home directory!
Sudo
The last piece of this puzzle we'll deal with here is sudo. As a common
example, we'll enable all members of the Domain Admins group to use sudo.
Rather than editing /etc/sudoers, we'll drop our custom sudo configuration
into to file in /etc/sudoers.d:
visudo -f /etc/sudoers.d/domain-admins
Add this line, of course replacing ONTHEFIVE with your domain realm:
%ONTHEFIVE\\domain\ admins ALL=(ALL:ALL) NOPASSWD:ALL
After logging in as a member of this group, you should be able to sudo!
Kerberos + SSH
Update: Louis van Belle suggested also adding these packages:
ssh-krb5- Updates
/etc/ssh/sshd_configand setsGSSAPIAuthenticationandGSSAPIKeyExchangetoyes. libpam-krb5
cp sshd_config sshd_config.before-ssh-krb5
apt install ssh-krb5 libpam-krb5
With this, you can use Kerberos to authenticate when SSH-ing to the DC!